Android Studio’s “Code contains easter egg” inspection
There’s an inspection called “Code contains easter egg” that comes with Android Studio. This one:
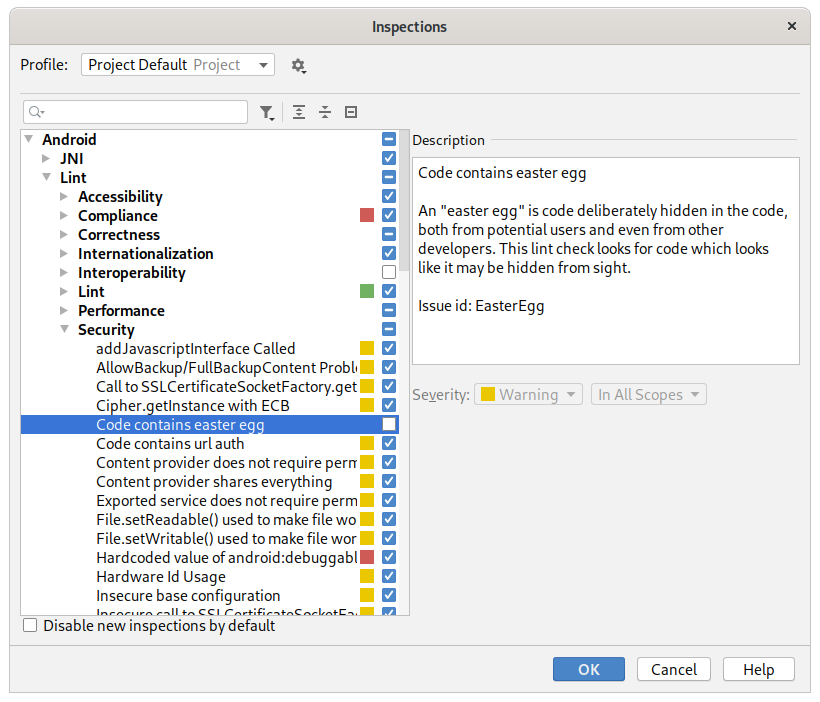
How can it systematically detect an easter egg?
It turns out that this inspection is limited to a narrow definition of an easter egg used in the inspection’s description. It finds a certain syntax of Java code that tries not to look like code, not features, like a flight simulator hidden in a spreadsheet program.
From the implementation of this lint,
we can see that it searches for the string \u002a\u002f inside a comment.
That’s some kind of escaped form of */.
Supposedly it’s correct to unescape these sequences before even lexing comments. But the syntax highlighting in Android Studio doesn’t behave this way.
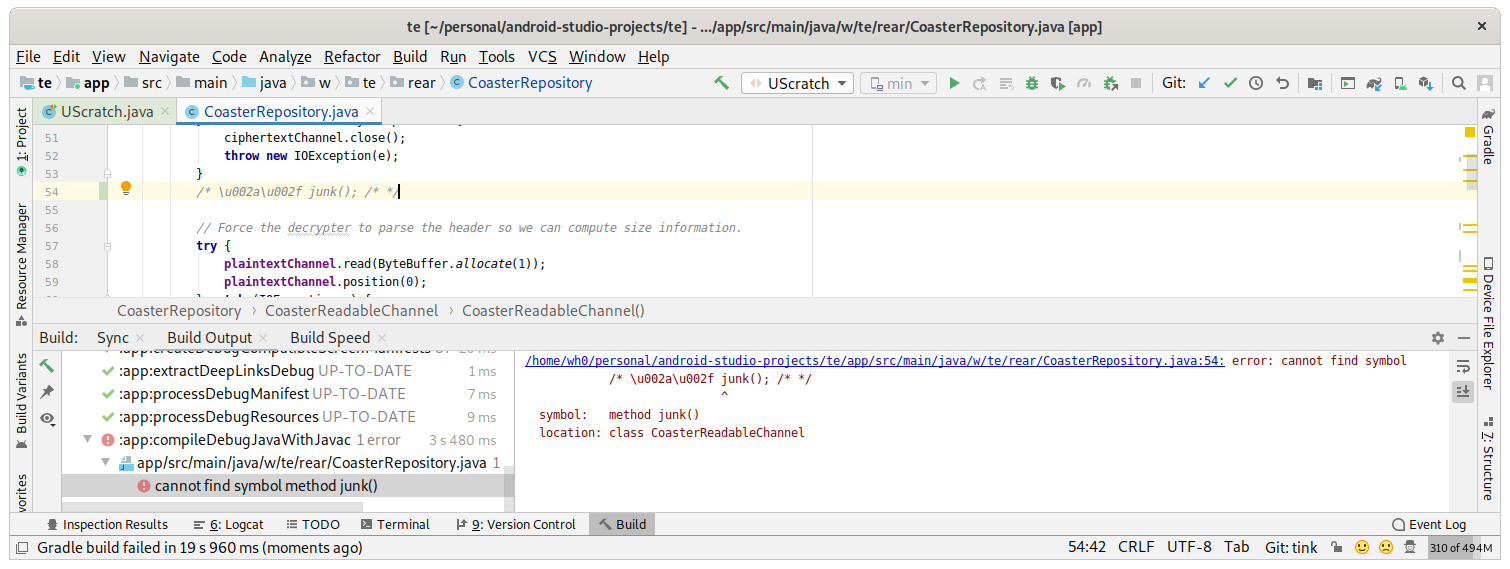
So indeed you might consider that code to be “hidden.”
Wait, does this mean Unicode string escapes aren’t actually parsed in the safe confines of a string literal?
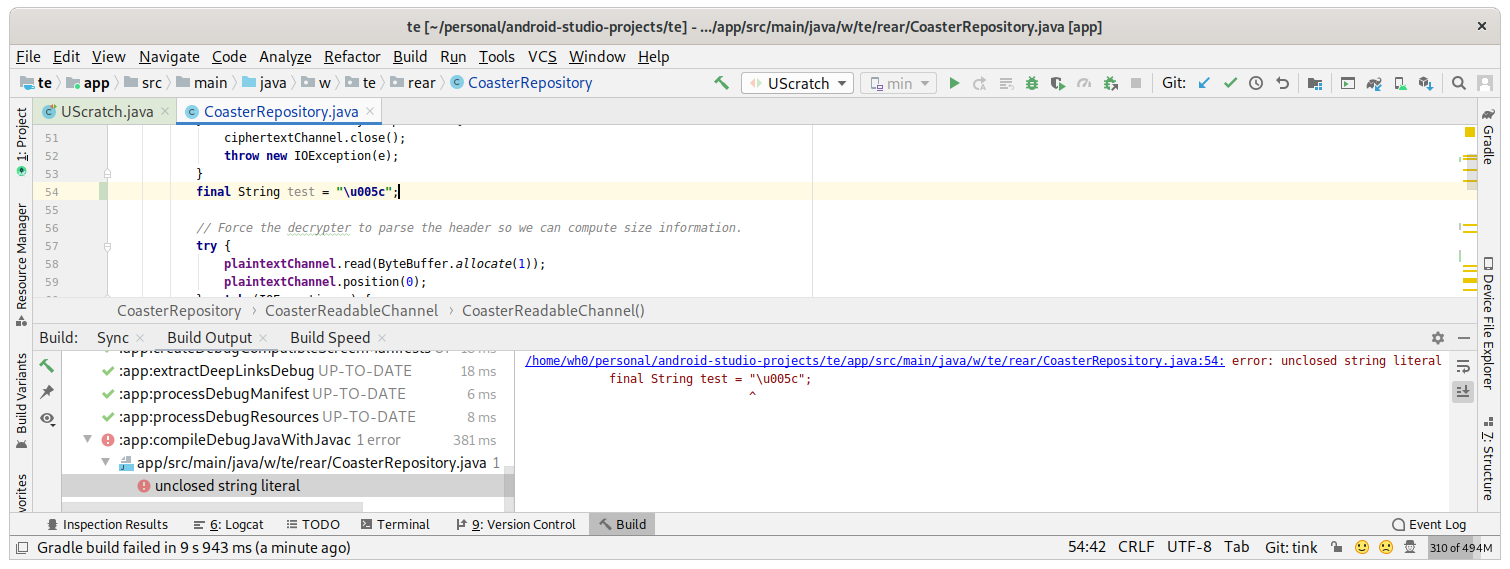
😱️
My last post was about either Wire toothbrushes or Rasterization of coincident edges. Find out which.